VERTU Web3 OS
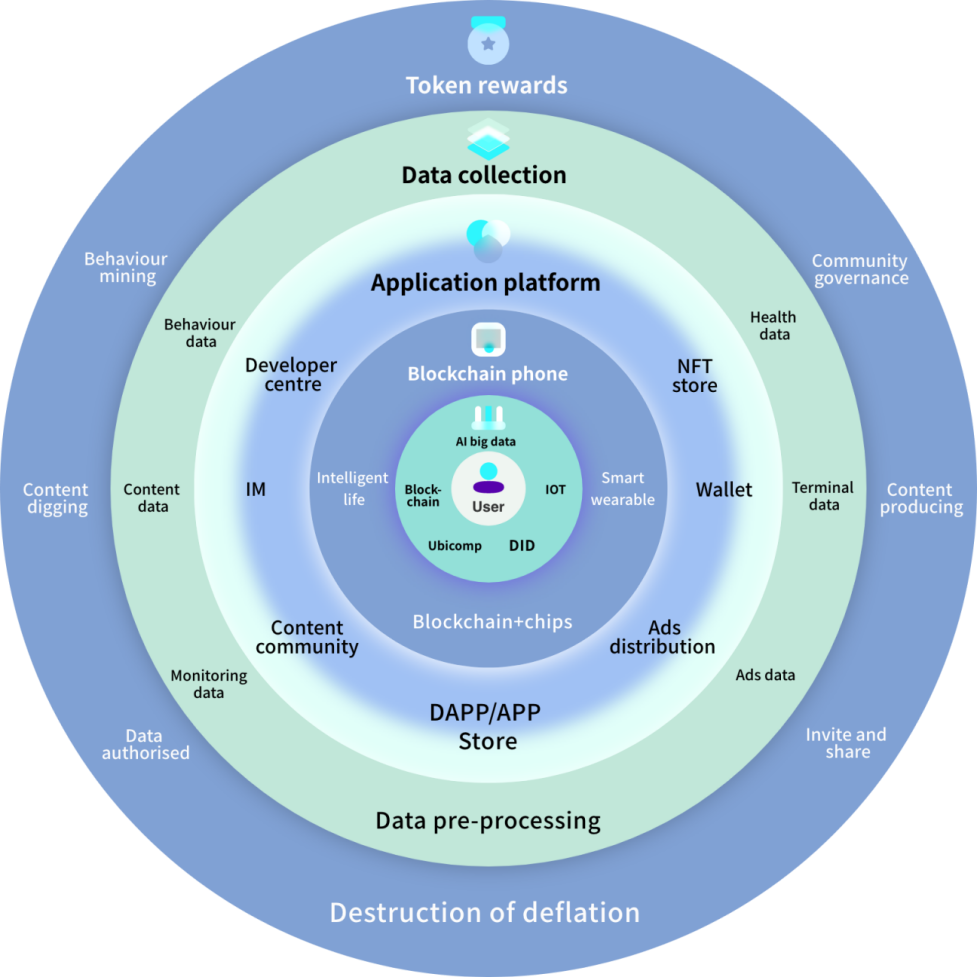
The most critical application of Web3 mobile phones is the need to establish a Web3.0 operating system based on mobile phone terminals, to coordinate the connection between various Web3.0 DApp applications inside the mobile phone and Ethernet, to deal with how to manage and allocate memory, to decide the priority of system resources supply and demand, to control input and output devices, to operate the network and to manage the file system and other basic matters. DApp applications should be able to help users use them to generate value and revenue, and together help build a win-win Web 3.0 value Internet world for all.
Web3 OS, created for Web3.0, provides a set of user-system interaction interface, which can be switched in the user's daily use of mobile phones with a single click. Users can enter the Web3.0 world while applying Web2.0 in a normal way, and it is very convenient to implement the basic applications of DID identity system and distributed storage. Web3.0 world, without having to consider the blockchain principle behind it, is very smooth to start using. This requires deep optimisation from the underlying driver to the system layer to the application layer, and reflects the win-win ecological advantages of Web 3.0 more than the traditional IOS and Android OS systems. Here, property will be protected, privacy will not be violated and data will not be misused, realising the ideal demands of decentralisation, privacy security and data autonomy for users.
Jack Dorsey once argued that Web3 is really all about decentralised identity and decentralised storage, and he believes that the spirit of Web3 is to bring data back into the ownership of the user. We highly agree with Jack Dorsey's description of the essence of Web3, and moreover believe that in today's world, our decentralised identity and decentralised storage need to revolve around the mobile phone. Each of us can't live without our mobile phones, and each of us is exposed to a wide range of applications through our smartphones every day, and we generate a huge amount of online and offline behavioural data while using these applications. Through such a set of operating system, the mobile phone will process the user behavioural data and then store and chain it in a distributed manner. These behavioural data and asset data can be managed and controlled by the user through digital identity and cannot be stolen by others.
Such an operating system is a new user-centric Web3.0 ecosystem in the world of Web3.0 Internet of Value, where technologies such as blockchain, AI, big data, IoT and pan-computing are organically combined with the Internet of Behavioural Value under the incentive of passwords. In this ecology, property will be protected, privacy will not be violated and data will not be misused; where everyone creates value together and shares the ecological benefits. We believe that only in such an ecosystem can the Web 3.0 network truly become an Internet of Behavioral Values!
Here, value is embodied, carried and transmitted, and is indispensable in the transaction. Value is one of the key factors involved in transactions, and it is an eternal proposition how to better embody value, ensure value, and better exchange value. The traditional Web2.0 Internet can solve the problem of information dissemination well, but it is difficult to ensure that the value of goods will not be damaged in the process of information transmission. The Internet of Value is a real Internet of value.
VERTU Web3 OS uses a blockchain architecture to secure databases and user accounts, unauthorized access and tamper-proofing can be prevented, while saving money for businesses that adopt blockchain technology. Blockchain creates tamper-proof logs, it constructs absolute and deterministic sequences to receive user input, and smart contracts provide deterministic business logic to ensure consistency across all systems.
Web3 OS runs a light Ethereum client as a system service, which means it doesn’t store all blockchain data, but it verifies all blocks for itself. An onboard Ethereum client brings a layer of abstraction and simplify in-app setup, Web3 OS users do not need to rely upon a third party service (like Infura or Alchemy) to interact with the Ethereum blockchain.
With advances in storage capacity, moving to a full node setup will become a feasible option, which will allow for a truly decentralized OS. Furthermore, each Web3 phone will improve the decentralization of Ethereum itself.
Web3 OS will feature robust wallet support. The goal is to enable a crypto-ready experience from the moment the phone gets turned on the first time. In addition to a built-in wallet that will come handy for crypto novices, Web3 OS will support some of the more popular wallets as well. Private keys will be hardware encrypted and stored, using the device’s built-in security chip, whenever possible. Connecting 3rd party wallets will be achieved through a dedicated protocol, where signature authorization will be deferred to the originating wallet.
Running a local node along with built-in wallet support will unlock many interesting use cases when it comes to the browser, from seamlessly connecting apps to injecting identity into the browsing session.
Additionally, the built in browser will come with IPFS and .eth domain support, which will allow for further content decentralization.
The VERTU Phone will enable novel economics and experiences. Apps, ERC20s, and NFTs will expand in potential when paired with the geolocation, camera, and near-field communication capabilities of mobile. New social and creative experiences will become possible, and will integrate seamlessly with the tokenization and financialization of the physical and digital worlds and experiences.
In the traditional Internet world, we are already familiar with Internet identities in the form of accounts such as phone numbers. These identities in different ecological strips are managed and kept by one corresponding centralized Internet service provider, and thus cannot avoid the corresponding centralized hidden dangers.
In addition to the right of these service nodes to close our accounts and make us lose our identities on multiple sites at the same time, the more serious problem is the collective privacy leakage — the centralized architecture is destined to make privacy leakage an unavoidable event once it happens.
DID (Decentralized Identifier), a decentralized identity system, uses blockchain and other technologies to make digital identity truly owned and controlled by the user, just as we keep our ID cards, passports, account books and other paper documents in our own homes, and only take them out when needed, without any intermediary in full possession. The user’s identity and data can better avoid the above dilemma.
So in the Web 3.0 times, with DID users will have more control over their identity and data, avoiding many disputes and maintaining the trustworthiness of data at a lower cost.
VERTU Ecosystem is also building a new network system and innovative ways to play based on personal identity through DID, allowing users to achieve true identity autonomy and control in the digital world, and to feel the pleasure and fun of the future digital world.
As the only identifiable identity of the mobile phone ecosystem, DID is the carrier for users to manage their assets and data, and it opens up the entrance to all applications of the ecosystem. The user can use the DID as an account to log in to all applications within the ecosystem, enabling anonymity of account information. At the same time, the information on the DID is chained to protect the security of user assets and privacy.
Underpinned by a blockchain security chip based on the TEE+SE Trusted Device Architecture, VERTU Web3 phone empowers its users through a DID allowing to give them control over their data, protect their privacy and ultimately ensure their freedom through an open, censorship-resistant network.
DIDs evolve and derive from traditional centralised identities. The move from centralised identities to DIDs has taken place through centralised identities, federated identities, user-centric identities and DIDs, with the specificity of DIDs being expressed in three dimensions: security, control and portability. Security in terms of protection, persistence and minimisation; control in terms of presence, control and permission; and portability in terms of transparency, interoperability, portability and access rights.
The DID architecture consists of four main components: network protocol, distributed ledger, DID protocol and application, the advantages of the DID technology stack are the governance structure, independent storage space, and less susceptible to network failure, etc. Its development is essentially the result of a continuous game between efficiency and equity. Technically, the development of DID will bring about advances in decentralised storage and cross-chain technology; application-wise, the future development of DID is predicated on the increasing desire for data equality.
The core objective of Web 3.0 is to assert the right of every individual to own and control his or her own digital identity, which can securely store elements of his or her digital identity and protect privacy, and ultimately empower its users by ensuring their freedom through an open, censorship-resistant web.
The participants in a DID system are the user, the identity, the initiator of the verifiable statement and the trusted party. The verifiable statement initiator initiates a verifiable statement of the user's identity after verifying that the user's specific attributes (e.g. gender, age, etc.) are correct. Any trusted party (verifier) that needs to verify the user will receive the verifiable statement and verify its authenticity. A prerequisite for the effective operation of this identity management system is that the trusted party must have a trusted relationship with the initiator of the statement. Assuming that Tom needs to register an account (identifier) with the identity management platform, and that in the DID system Tom has control, ownership, use and access to his own identity and its associated data, when the statement initiator issues the statement "Tom has registered an account with an ID identifier", the identity must be presented to a verifier who has established a trustworthy relationship with the statement initiator and who can objectively verify the authenticity of the statement.
The DID management system architecture is based on a distributed ledger based on blockchain technology and the DID protocol. Clearly, the DID system is user-centric. the DID system operates in the flow shown in the diagram and has the following characteristics.
The user has absolute control over the database in which the authenticable statement is stored. The identity verifiable statement is stored in a user-controlled store (typically a database), usually off-chain for the protection of the user's privacy, and the encrypted information is abstracted to the chain. The trusted party (verifier) can compare the publicly available identifier with the identifier in the statement submitted to him by the user. After authenticating the user using the authentication methods provided in the public chain, the statement itself can be verified by the trusted party (verifier), ultimately giving a result of passing or rejecting the authentication.
The blockchain not only has the function of providing the user with the ability to register an identifier on the chain, but also allows the user to register verifiable statements by proxy and encrypt them. On the one hand, the user, on the basis of providing personal information minimisation (satisfying the function of being able to determine whether the user is able to register an identifier), stores the user's identifier and the relevant digital certificate encrypted on the chain, and each node keeps track of it; on the other hand, the user agent stores the registration verifiable statement on the chain as well, and encrypts the verifiable statement through asymmetric encryption technology to further The privacy of user data is further protected by encrypting the verifiable statement with asymmetric encryption technology.
There are many components to the technology stack of a DID system, which vary considerably from project to project, but the basic components are essential. The components that are common to all projects are the base components and the optional components. Generally speaking, the technology stack of a DID system is structured from the bottom up, with the network protocol (typically TCP/IP) at the bottom, the blockchain or distributed ledger at the top, the DID protocol at the top and the application software (DApp, App, etc.) at the top.
DID adheres strictly to high standards of privacy protection protocols such as GDPR in terms of compliance. By establishing a mechanism for data use based on user permission, users can provide information appropriate to their actual situation and complete the exchange function of verifiable statements so as not to reveal other core information such as ID numbers, mobile phone contact details and dates of birth. At the same time, regulators or authorities can be made to act as verifiers, which facilitates regulation and reduces the scope for money laundering and crime.
DID raises the cost of malicious nodes by storing a summary of user activity in the form of table headers on the blockchain and establishing an effective monitoring and consensus mechanism through a distributed ledger, so that if a malicious node wants to steal user information and digital currency assets through hacking means such as a 51% attack, its actions will be immediately revealed by multiple verifying parties.
We believe that an autonomous identity system based on multiple public blockchains needs to be built into the Web3 mobile operating system in accordance with DID. The system is based on an autonomous identity protocol on the underlying hardware of the mobile phone and has 3 main functions: a multi-chain wallet, a trust network and reliable storage of data. Of these, the trust network should consist of two parts: identity accounts and verifiable statements. The identity account plays the role of a node in the trust network, while the verifiable statement is the link between the nodes. The identity account consists of an identity name, an identity file, and a data security zone (identity contract control, based on secure data storage). The peer-to-peer bi-directional structure of the trust network makes forgery invisible. The trust network effectively identifies disinformation, fake news and fraud created using image and voice synthesis technology, reducing friction caused by lack of trust in collaboration. The Chain Wallet serves wallets from multiple known public chains and supports multiple smart contract platforms. Multi-chain wallets have the following features: a unified identity name, free usage credits (lowering the threshold for usage and measuring it in network fees - access), checks and balances on each other's permissions designed to secure accounts, recovery mechanisms for lost private keys, scalability of protocols, anti-spam transactions, and the ability to implement DIDs by way of central conversion Passes can be used on multiple chains.
Of course, such a DID system would need to meet the standards set by the W3C, linked to the Decentralised Public Key Infrastructure (DPKI) metadata, which consists of a document containing the public key material, the authentication descriptor and the server-side DID. However, in contrast to the traditional W3C proposed DID standard, which is not centrally hosted, but rather enables autonomous user identity management entirely through smart contracts, it should contain the following four innovative features.
Permission splitting setup. The user's on-chain permissions need to be split into administrative and operational permissions. Operational permissions are used for day-to-day operations such as transfers, pledges, etc. Administrative permissions are the highest permissions on the account, but administrative permissions can only modify the user's permissions, not directly manipulate account assets or daily operations.
Hierarchical key management. Once exported, the management private key (recovery code) is stored offline forever and is managed using a hardware wallet. The operational private key is tied to the user's smartphone SE+TEE private computing environment, so that the user does not need to care about the technical implementation details, but only needs to provide the account password or the correct biometrics to retrieve the operational private key.
Trusted recovery mechanism. To avoid the immediate consequences of private key loss, the DID protocol requires a certain delay when replacing the private key. At the same time, an emergency contact mechanism is provided. After the off-chain authentication, a set of emergency contacts with a threshold number can help to quickly replace the key, and can also help to regain management rights (with a delay) when the management private key is lost. In addition, the DID smart contract is open source and audited by authorities to avoid code vulnerabilities to the greatest extent possible.
Risk response systems need to be in place. Combining the previous points, there needs to be solutions for risk events in cases of user negligence, hacking and theft, which can deal with most problems such as lost phones, forgotten passwords, lost recovery codes and stolen recovery codes.
Further, we believe that such a set of DID identity systems for the Web3 mobile operating system needs to actively embrace the SBT initiative and participate in the co-construction of a censorship-resistant, bottom-up alternative to a top-down credit system for business and society. SBTs representing educational credentials, previous employment history and leases can be used as long-term credit-related records, enabling 'souls' (accounts) to obtain loans by using meaningful reputation, thus avoiding collateral requirements. Loans and lines of credit can be expressed as non-transferable but revocable SBTs, so that loan lines can be embedded in the SBT of a particular 'soul' (account) - as a form of (non-forfeitable) reputation collateral - until they are repaid and subsequently destroyed (or, better still, replaced by a 'proof of repayment' to increase the 'soul's' credit history).
Web3 has built a parallel financial system with unprecedented flexibility and creativity in less than a decade, and has created a complex and open ecology of financial transactions. However, financial transactions rely on economic values that are generated by people and their relationships. Because Web3 lacks an original language for representing this social identity, Web3 has become fundamentally dependent on the very centralised Web2 structure that it wants to transcend, thus replicating the limitations of Web2. For example, the lack of Web3's native identity and reputation forces NFT artists to often rely on centralised platforms such as OpenSea and Twitter to promise scarcity and initial provenance, and discourages forms of lending that are not fully collateralised.
Web3 aspires to transform society broadly, not just the financial system. However, today's social structures - families, churches, teams, companies, civil society, celebrities, democracy - make no sense in a virtual world without the original languages that represent the human soul and the wider relationships they support.
If Web3 eschews persistent identities, models of trust and cooperation, and combinable rights and licences, we will see witch attacks, collusion and a limited economic field of fully transferable private property, all of which will tend towards 'hyper-financialisation'.
To bypass hyper-financialisation while unleashing exponential growth, we believe it is possible to enhance and connect our sociality in virtual and physical reality through a Web3 mobile phone, empowering souls and communities to encode rich social and economic relationships. But it is not enough to build on trust and cooperation. Correcting the tendency to bias and over-coordinate (or collude) between networks of trust is essential to encourage more complex and diverse relationships that span greater social distances than ever before. We call this the 'decentralised society (DeSoc)': a co-determined sociality where souls and communities come together from the bottom up as emergent properties of each other to produce plural networked products at different scales.
We believe that such a Web3 phone with a built-in DID+SBT model would be very helpful to DeSoc, as the web is the most powerful engine of economic growth, but is most easily captured by private players (e.g. Web2) and powerful governments. The most significant economic growth comes from the increase in network revenue, with each additional unit of input generating more output.
Imagine a world where most participants have 'souls' (i.e. accounts) in which SBTs (soul-bound Tokens) corresponding to a set of affiliations, memberships and certificates are stored. For example, a person with a 'soul' (account) might store SBTs representing educational credentials, companies he has worked for, artworks he has written or books. these SBTs in their simplest form are able to 'self-authenticate', in the same way that we share information about ourselves in our CVs, which is more meaningful in the DID ecosystem. But the real power of this mechanism becomes apparent when SBTs held by one 'soul' (account) can be issued by other 'souls' who are counterparties to these relationships. These counterparty 'souls' may be individuals, companies or institutions.
The non-transferable nature of SBTs - such as one-off educational certificates - raises an important question: How can you not lose your 'soul'? Today's recovery methods, such as multiple signature recovery or mnemonics, have different trade-offs in terms of psychological load, ease of processing and security. And our proposed social recovery DID mechanism solves this problem perfectly. Allowing social recovery is a good starting point to ensure security, with the 'soul' being the cross-vote of its social network. Users manage a set of 'guardians' and give them (based on an absolute majority) the power to change the wallet secret key. These guardians can be a mix of individuals, institutions or other wallets, and successful social recovery depends on curating and maintaining a trusting relationship with the majority of guardians.
The DID identity system in the Web3 mobile operating system allows the recovery of 'souls' (accounts) to be linked to their membership of the mobile address book, using the maximum extensive real-time relationships for security. Through the mobile address book, individuals have access to a more secure and extensive off-chain communication channel than the blockchain itself, where 'authentication' (through conversations and shared secrets) can take place undoubtedly more securely and effectively.
It is with such a DID+SBT system design that we believe the Web3 mobile phone can become a solid underlying hardware infrastructure for the Web 3.0 world. After all, we all understand that software is eating up the world and that the digital world will have an increasing proportion in the future, but the digital world and the physical world should not be separated, and an efficient connection between them needs to be made with the Web3 mobile phone's DID+SBT SBT to achieve this. This connection, not only between the physical and digital worlds, but also between the digital worlds, is the only way to connect the physical and digital worlds with the various "credentials" based on DID+SBT.